Using
Suggest editsThese use cases show how Imperva Data Security Fabric monitors an EDB Postgres Advanced Server database. You can configure many different options and reports with the Imperva Data Security Fabric Agent installed on your EDB Postgres Advanced Server or PostgreSQL database.
Some of these options are:
- Scan and assess the servers.
- Configure security policies.
- Create and manage reports.
- Configure and view audited traffic.
- Configure or work with a database cluster.
For in-depth information on the many pieces of database activity monitoring with the Imperva Data Security Fabric agent, see Database Activity Monitoring User Guide on the Imperva website.
Monitor EDB Postgres Advanced Server or PostgreSQL database traffic
One of the uses of the Imperva Data Security Fabric agent is monitoring database traffic for compliance and auditing. Many regulations and industry standards require organizations to monitor and track data access and changes for auditing purposes. This can include tracking access to sensitive data, such as financial information or customers' personal data.
You can use Imperva agents within the Imperva Data Security Fabric solution to track and review the actions of employees and third parties to ensure they're complying with policies and procedures.
Setting up to monitor database traffic with Imperva Data Security Fabric agent
Set up the Imperva Data Security Fabric agent to monitor EDB Postgres Advanced Server traffic.
Install Imperva Data Security Fabric agent.
Run the basic management configuration.
Connect to the database using an external client, and run queries.
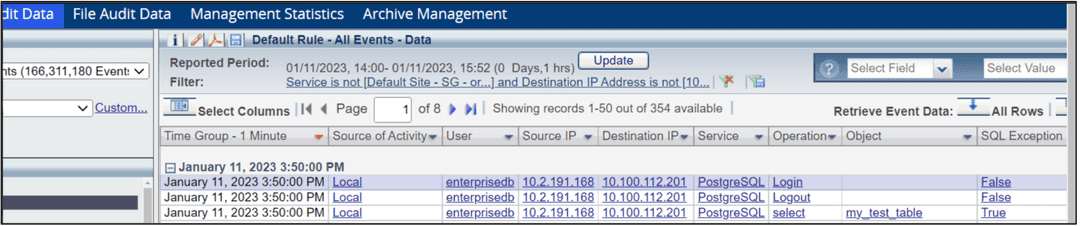
Check that the traffic was intercepted and displayed in the management audit screen.
This example shows a query to table name my_test_table. The database is PostgreSQL. The table doesn't exist, so the SQL exception is marked as true.
Secure an EDB Postgres Advanced Server or PostgreSQL database
You can also use Imperva agents within an EDB Postgres Advanced Server or PostgreSQL server for security reasons. You can use Imperva agents to block transactions like unauthorized access or changes to data, which can help to protect against data breaches, cyber attacks, and other threats.
Imperva Data Security Fabric agent traffic block conditions
An Imperva agent within the Imperva Data Security Fabric Solution can block traffic when all the following conditions are met:
An applicable security policy blocks the traffic.
Enable Blocking is selected on the Imperva Agent's Settings tab.
The server group isn't in simulation mode.
When Enable Blocking is selected, Default Connection Mode in Imperva Agent’s Settings tab must be set to either Sniffing or Inline. In both cases, Imperva Agent forwards the traffic to the gateway.
If Default Connection Mode is set to Sniffing, then Imperva Agent allows the traffic to pass to the database. If Imperva Agent later receives a notification from the gateway that the traffic must be blocked, it does so. However, in the meantime, some undesirable traffic can get through to the database.
The advantage of Sniffing is that it doesn't introduce latency. Its disadvantage is that undesirable traffic can reach the database.
If Default Connection Mode is set to Inline, then Imperva Agent holds the traffic until it receives a notification from the gateway indicating whether to allow or block the traffic.
The advantage of the Inline option is that no undesirable traffic can reach the database. The disadvantage is that it introduces latency.
For more information
See the Imperva Database Activity Monitoring User Guide on the Imperva website.
export const _frontmatter = {"title":"Using","description":"Walkthrough of example usage scenarios"}
Could this page be better? Report a problem or suggest an addition!